Architecture Diagrams¶
1. Where we are now, and where we are going¶
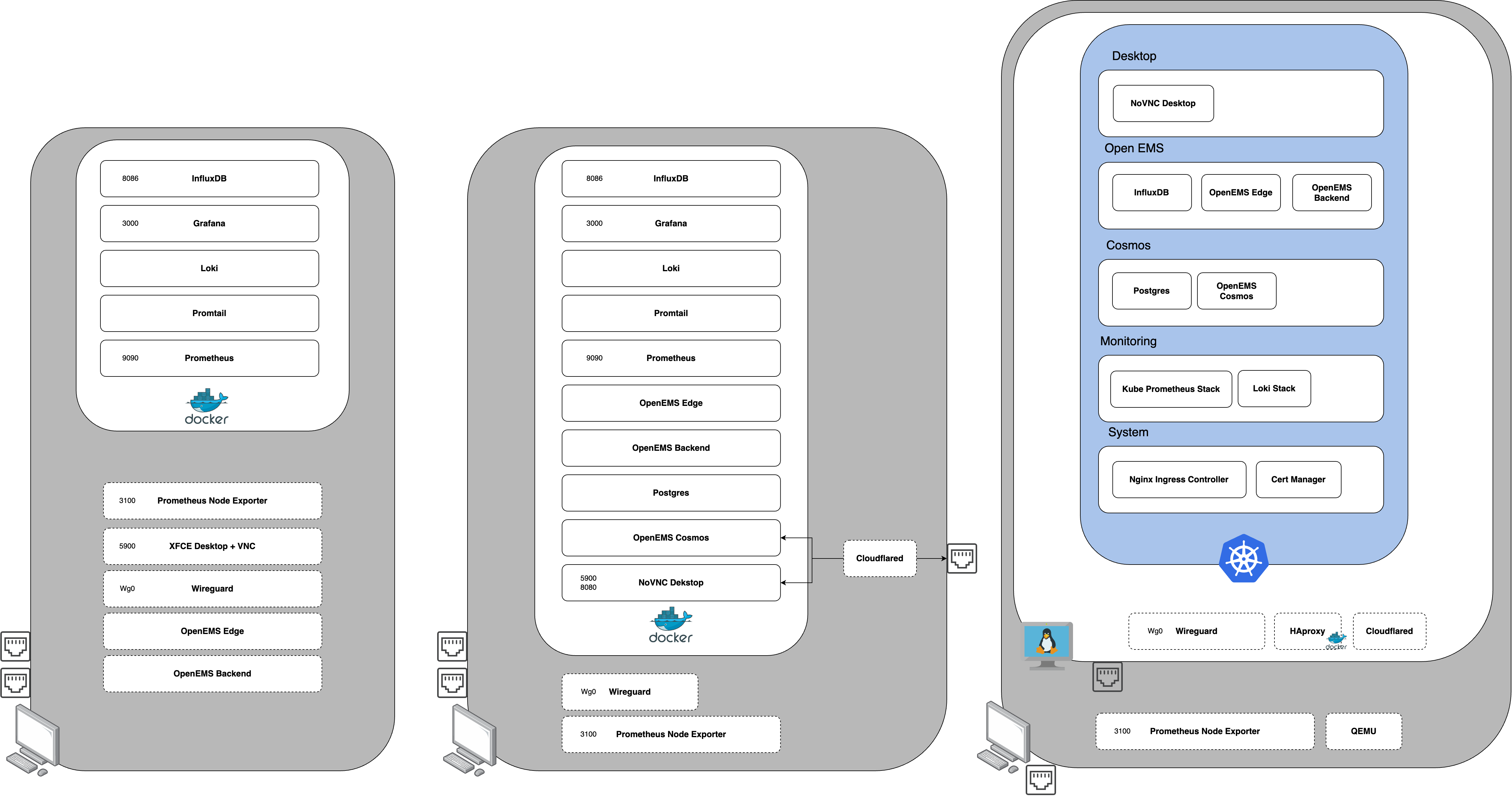
As we continue to containerize our applications, we can migrate more services into docker-compose. The desktop can now be containerized and access via a web endpoint which removes the need for a VNC client. The new front-end can also be deployed along with it's postgres database. A new connection-method via Cloudflared tunneling is possible now.
Our eventual goal is to have all of our services containerized and able to be migrated into Kubernetes. The cluster can then be placed in a virtualized-host and be fully decoupled from the physical hardware. This will allow us to deploy use a single architecture on both the edge and in the cloud.
2. WireGuard-Based Networking¶
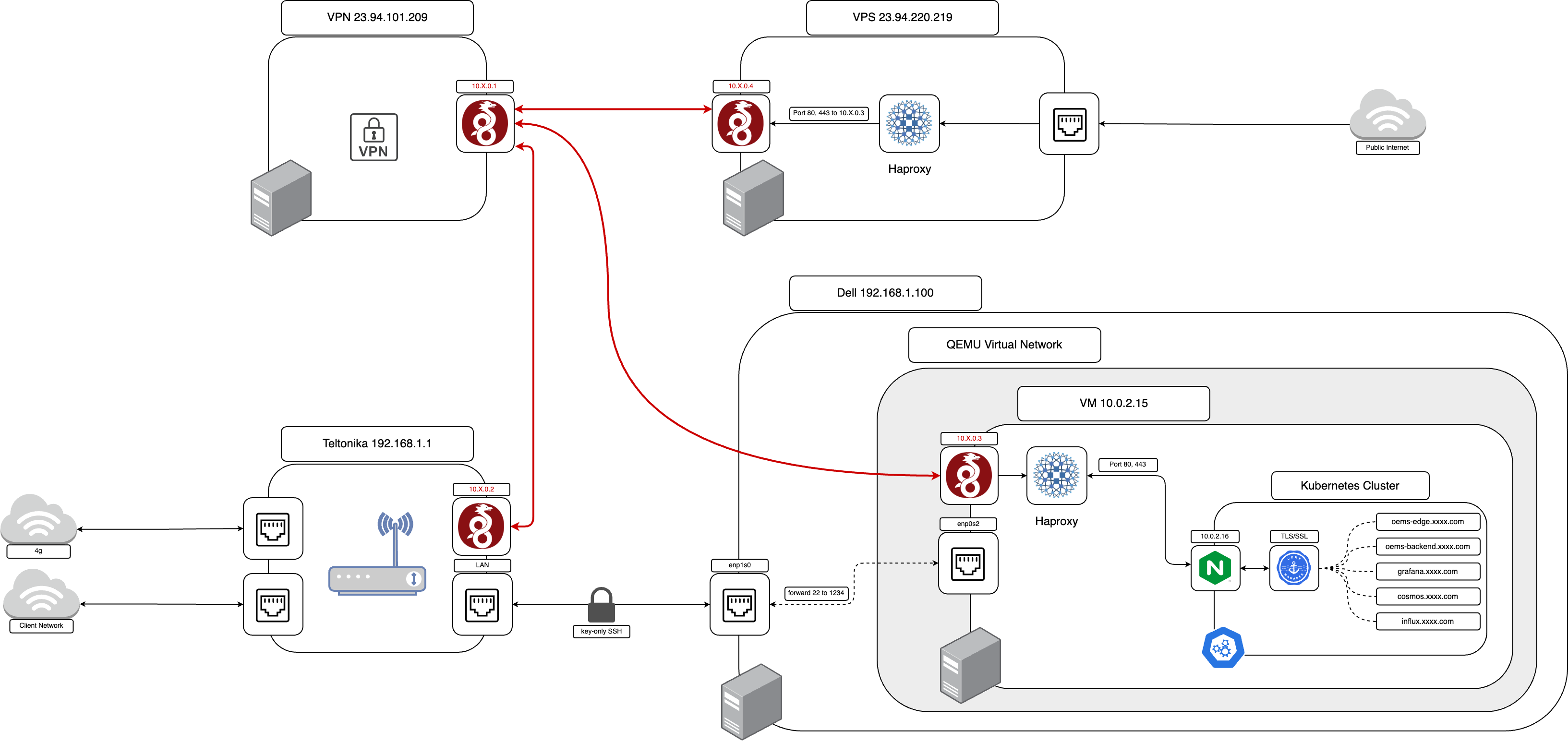
This diagram shows how a WireGuard-based VPN solution can be used in conjunction with HAProxy to deliver end-to-end encrypted traffic from a client to Nginx where TLS termination is handled via Cert-manager. The merits of this solution lie in the use of all FOSS tooling which can prevent vendor lock-in and keeps license fees to a minimum. Additionally, WireGuard is generally considered to be cryptographically superior to SSH tunneling alone.
3. Tunnel-Based Networking¶
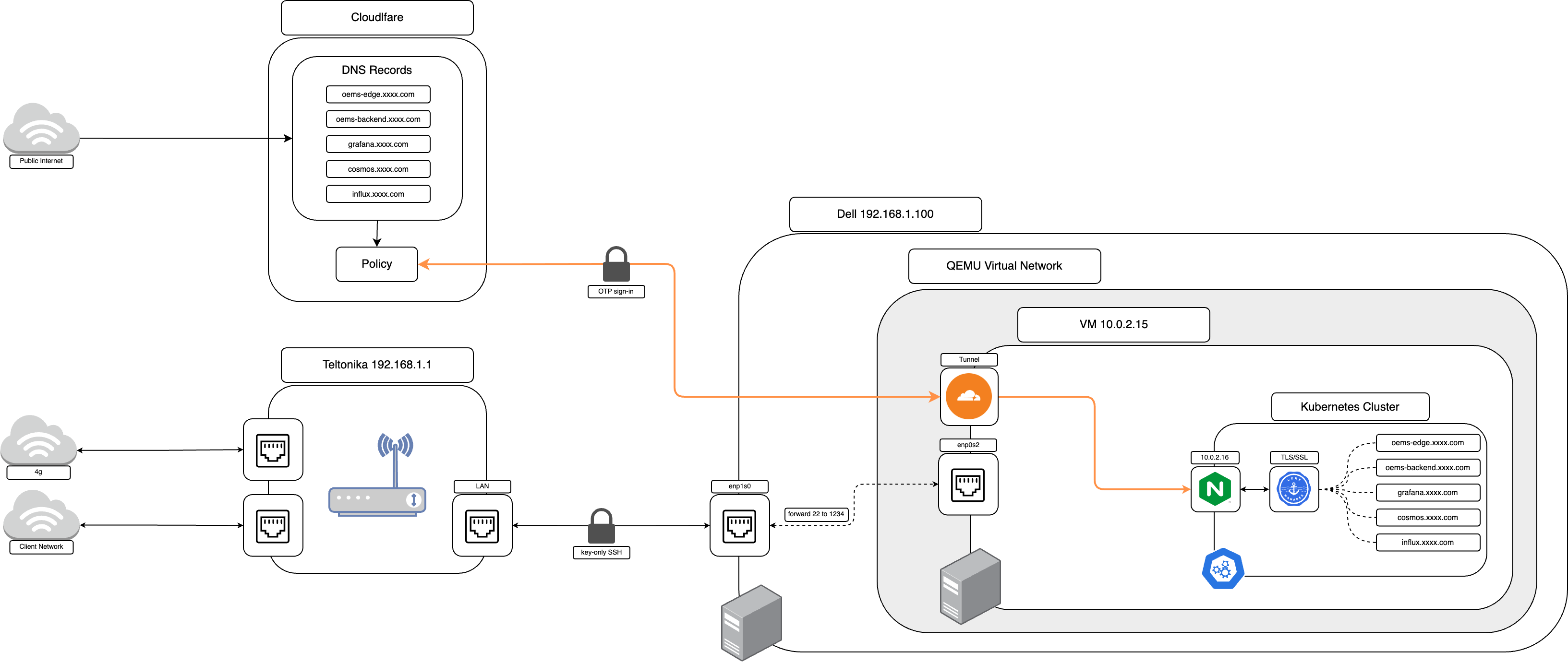
This is a simplified version of the previous design based on using the CloudFlared tunnel. The need to maintain a VPN and public endpoints is removed and replaced by using the Cloudflared tunnel installed into the virtual-machine, and managing the routes via the Cloudflare 0trust portal.
While some complexity in terms of infrastructure is removed, it is shifted into the management of tunnels, policies, and routes via CloudFlare's portal. This could become quite burdensome at scale as each client may require as many as 5 domains per edge-device. Additionally, this leaves us susceptible to vendor lock-in and fee changes because the service is only available for sites hosted with Cloudflare themselves.
4. Original Proof-of-Concept¶
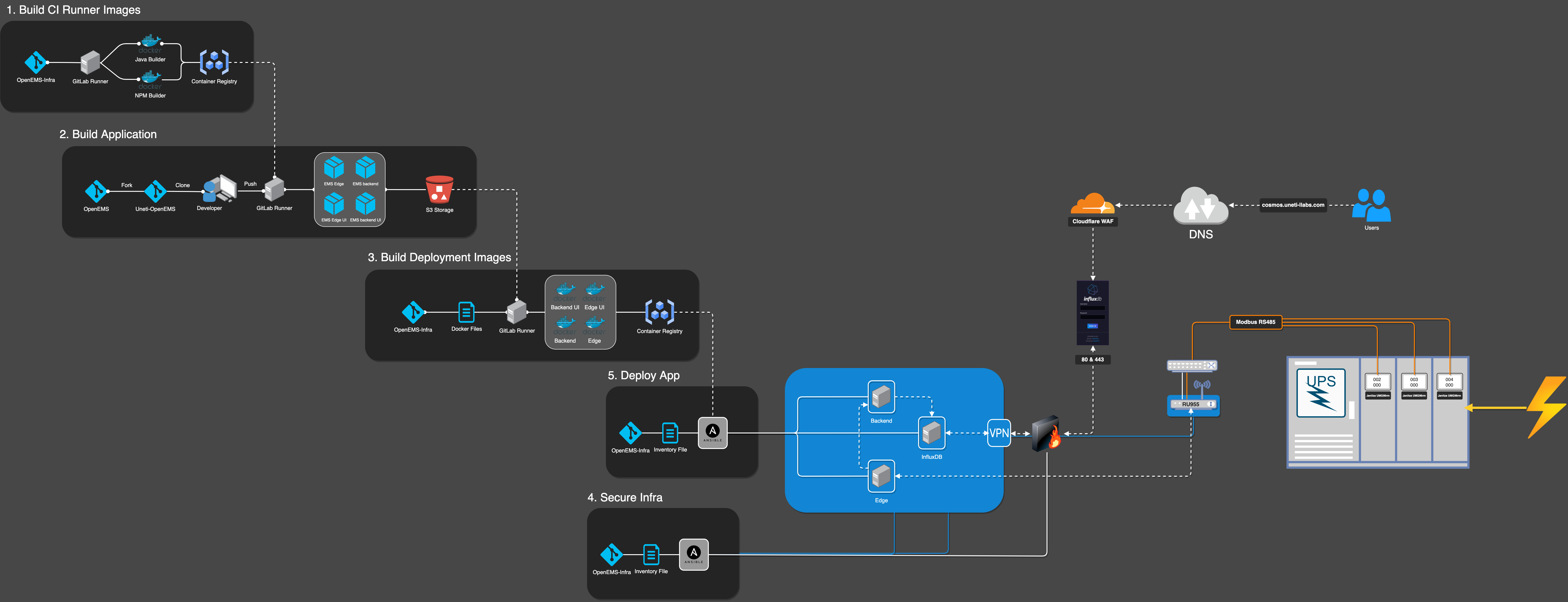
This original chart tries to map the complete environment of our pilot location. CI/CD tasks create images and load them into a container registry which will be used by an ansible application to deploy services into a dell machine at the edge. The Dell receives modbus data via the Teltonika router it is connected to. The Dell and Teltonika are secured via a WireGuard VPN.
This design has been phased out in favor of a docker-compose based deployment.