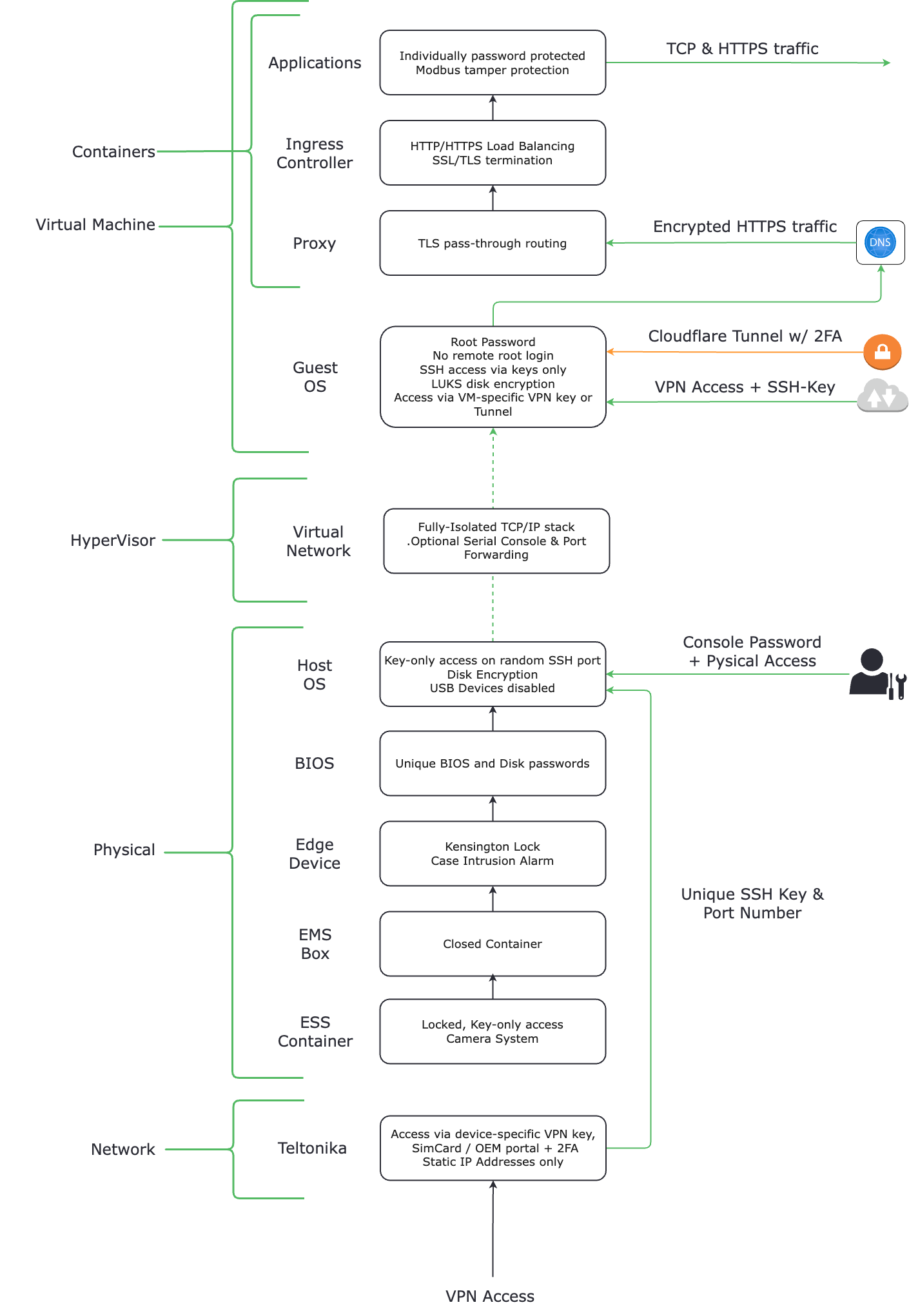
Security Diagrams¶
There are several access points to our architecture:
- The Teltonika router may be access from the network-provider's portal, as well as over the VPN via SSH.
- The Dell may be access via SSH though the teltonika router using the local network. Additionally, a user with physical access to the terminal may use the root credentials to log-in.
- The virtual machine may be access via port-forwarding from the dell, an emulated serial console via QEMU, a VPN connection, or through a tunnel.
- Individual applications and services may be accessed via HTTPs over the internet and are password protected.